- Published on
Tycoon PAAS Evolves
- Authors

- Name
- Joshua Rawles
Introduction
In Feburuary, 2024 TrustWave posted a very detailed article regarding the group Tycoon. Tycoon is a group that provides Phishing-as-a-Services (PAAS) to paying "customers". The infrastructure will be set-up to this group and a "link" is provided, however the phishing lures will need to be set-up by the buyer. In our previous article surrounding this group, we made comments saying that they had not been active around the start of May, however, we have started to see a rise in activity from this group again with a new name "RaccoonO365" with similar phishing portals and a slightly new user-agent string during the portal sign-ins "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36". This was determined to be a False Positive and is still infact part of the Tycoon Group, RaccoonO365 was using this as fake advertising (which I fell for)
Telegram
In May 2024, Tycoon Group made a post on their telegram chat with a disclaimer about a new service "RaccoonO365".
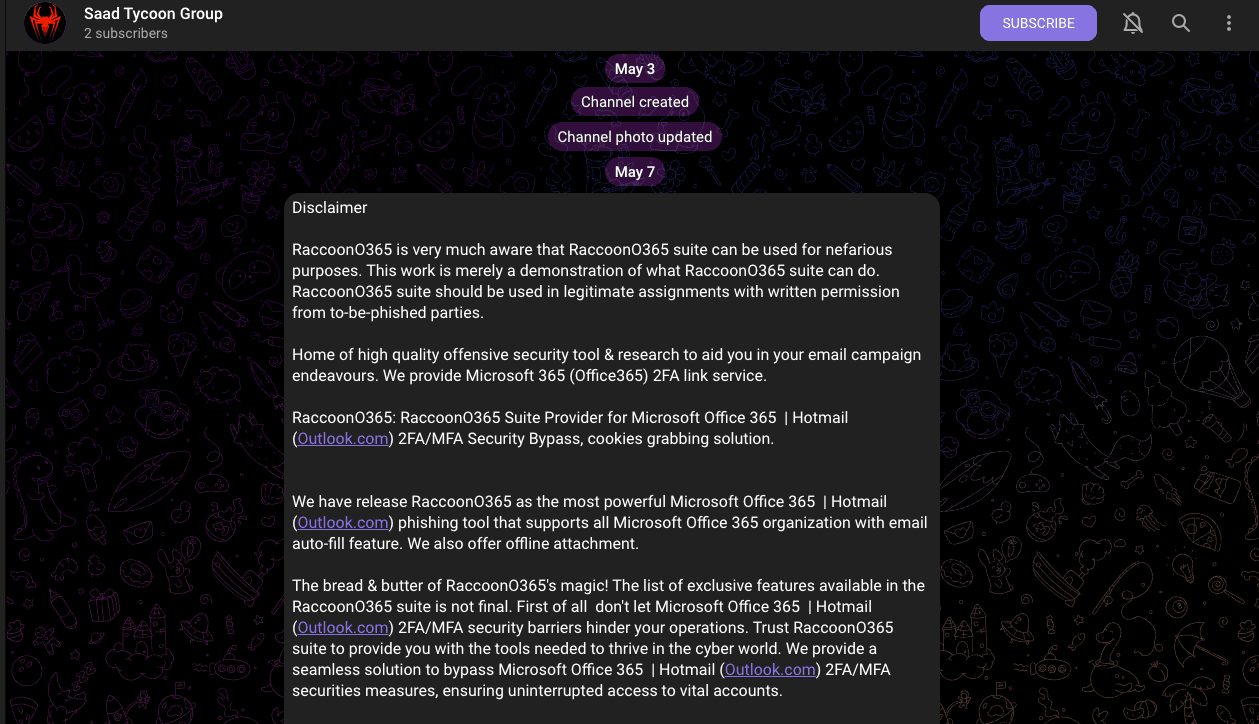
This service boasts the ability to bypass 2FA/MFA for Microsoft Office 365 along with updated tool abilities such as:
- Grabbing 2FA/MFA cookies
- Antibot Protection
- Undetected Links
- Auto-Grab Email Features

Although I havent gone as far to purchase a subscription for this to test it out (with the steep price of $170 USD per week) I believe to have found some evidence of "updated" phishing portals which work in much the same way as previously discussed. Other researchers let me know that this was infact still Tycoon Group and not Raccoon.
Initial
As always we have the initial link through a basic "HR" related phishing email. The specific URL was shortened using a "Cuttly" URL shortener to avoid looking suspicious.
Once redirected through the URL shortener the lure was hosted on an inauspicious "sharepoint" that appears to be hosted by possibly another "compromised" user. It appears it is common practice by some threat actors to do this to avoid exposing public facing infrastructure or for more targeted phishing campaigns.

Evasion
As usual once the user clicks on "Click View and Print Online" they are re-directed to a "cloudflare" verification, yes this is starting to sound all too familiar.

To avoid repeating what was discussed in the previous blog let's compare what we see during this attack.
The same encoded javascript which loads the cloudflare prompt in the website has the same obfuscation. However, this time we checked the output by just simply running a console.log(). It is just loading the cloudflare turnstile API with the requirements of the attacker.
- Turnstile is Cloudflare’s smart CAPTCHA alternative. It can be embedded into any website without sending traffic through Cloudflare and works without showing visitors a CAPTCHA.
By reviewing the code we also observe a few interesting variables being saved regarding your session.
- IP Address
- User Agent

The Phish
Again, once accepting the prompt the user is redirected to the main phishing portal, or well rather "allowed access", again this appears as the most up-to-date Microsoft sign-in page with not too many differences as before. From here to process is extremely similar except this time I do not see the initial loading of the obfuscated javascript in the sources or networks, however the massive xor value one containing all of the website features it still present and is basically the same as before.

So is there anything new this time? Well if we can remember RaccoonO365 stated that they can utilise the "auto sign in feature" if a username is included in the phishing portals url, lets test this out.
- First we added the required function to the end of the URI of the phishing portal.
- Then when visiting although with a tiny bit of lag it did indeed try to sign-in.
- Password is prompted afterwards.

It appears that this is controlled by another randomly named javascript that is imported in the initial loading of the website. However, this time we can see it referencing the "email-decode.min.js" which is confirmed to be cloudflares "Scrape Shield"". However, it seems in this code it is utilised in conjunction with the loaded .js to assign the email name to a variable to to sign-in automatically. This feature can be useful for attackers in direct spear-phishing attempts, to make the portal look just that little bit more legitimate.

Following this, the same websocket exfiltration is utilised as always, i couldn't find evidence of any "cookies" going out at the time though either because I hadn't had any saved, or that it is captured on the "server" side after MFA is accepted since MFA was prompted for this time.

Once MFA is accepted the user is redirected to gmail login page. The redirect can be observed also being applied in the network logs (search for "redirecturl:").

PAAS Notifications
After the "phish" is completed a notification will be sent to whomever is utilising the specific PAAS service. This will include information such as:
- Location Data
- User-Agents
- Passwords
- Cookies



Azure Logs
The logs are extremely similar again, with sign-ins to OfficeHome with a linux user-agent string. However, this time the user agent has a slightly different chrome version:
- Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36
The same problem with my MFA occurred again where my MFA was not applied the first time I signed in, whereas other times it was prompted. Really need to have a look into this at a later date....

OSINT
Now lets have a little look at the domain "persiat[.]com". Doing a quick domain age check we can see that this specific domain was registered on the 14th of May which matches with the resurgence of Tycoon and the rise in phishing attempts.

When attempting to have a look at some domain history with "Sublist3r" I did not get any results for it.
- Sublist3r is a python tool designed to enumerate subdomains of websites using OSINT. It helps penetration testers and bug hunters collect and gather subdomains for the domain they are targeting.
Referring back to our trusty virustotal I did observe some other sub-domains that fall under persiat. It appears that only some of these phishing portals subdomains are currently detected. This is likely a tactic to extend the life of a domain, before a new one needs to be "purchased". All sub-domains for this portal (that i could find on osint so far) contained the URI component "/cQ971y" at the end otherwise the domain becomes unreachable. It is quite uncanny to how "evilginx" urls work with "phishlets".

Conclusion
From how this portal works almost exactly like the previous Tycoon PAAS portal to the updated user-agent and the identification of some new features (such as the auto-grab email feature). I expect to see this picking up more and more "users" over the next few months. The main difference to look out for will be the updated Linux user-agent (which is already causing alot more False Positives).
- Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36
Perhaps in the future as this is tracked further we might find some re-occurring ISPs or future user-agents that can help in detecting these portals and sign-ins.
References:
- https://ig3thack3d4u.com/blog/Azurex11TycoonPAAS
- https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/breakdown-of-tycoon-phishing-as-a-service-system/
- https://developers.cloudflare.com/turnstile/
- https://github.com/aboul3la/Sublist3r
- https://blog.josephscott.org/2019/01/22/cloudflare-injected-javascript/
Credits: Shout-out to my anonymous co-worker for finding these guys on Telegram and letting me know about it (you know who you are ;))