- Published on
Testing MFA for M365 after unexpected results.
- Authors

- Name
- Joshua Rawles
Introduction
In our previous articles on RaccoonO365 I noticed a problem where authentications to an account with MFA applied were coming across as "single-factor-authentication" when signing in to OfficeHome aka Microsoft 365 . My first thought is that a cookie was stolen but then i remembered that I hadn't signed in at all prior to the testing from this account so I wanted to find out more.
MFA Original Set-Up
When creating my account, I registered for MFA with the normal means in the initial user set-up. With the "this workspace requires MFA" etc prompt.
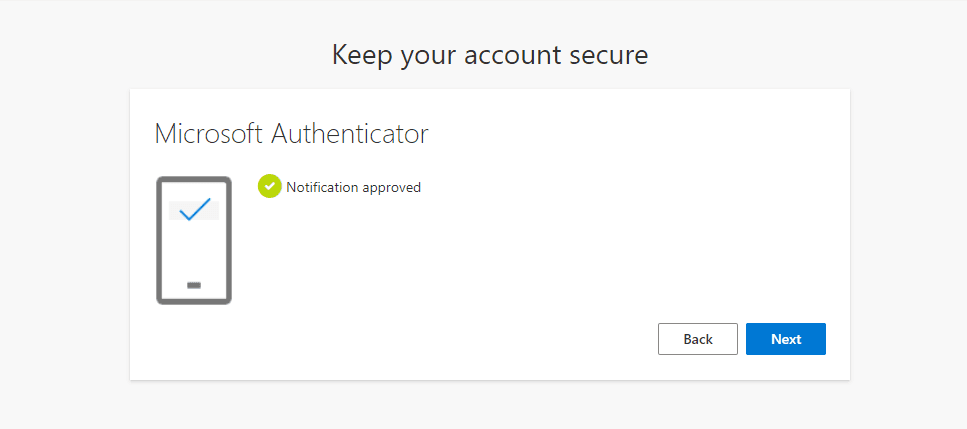
This is prompted because security defauts was enabled in my estate requiring all users to register for multifactor authentication. This is the main MFA solution for Organizations using the free tier of Microsoft Entra ID licensing, requiring users to register within 14 days.
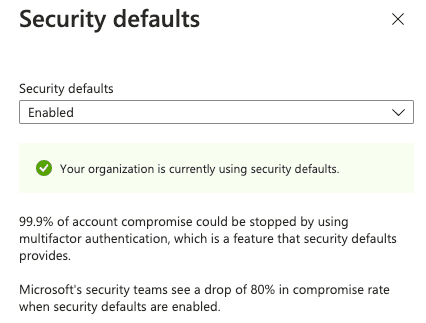
First Test (Fresh Account - Security Defaults)
I then proceed to sign-in from a different device and confirmed that it did not prompt me for MFA. This is a little bit awkward as most people would expect this to work. Confirmed in the logs that I got a "single-factor-authentication" sign-in event.
Second Test (E5 License Applied - FP)
At this time the user did not have a license applied to them, so I went ahead and added the M365 Developer license, this will add all the applications like outlook etc.
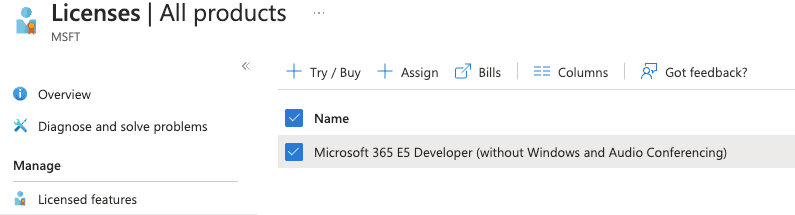
This time I tried logging in after revoking sessions and guess what, I was prompted for MFA. Guess they only thing was the license, perhaps you need the Azure M365 License applied for MFA to work.
Although excited that this worked I found out that i had signed into the Azure Portal instead of OfficeHome this time. So going to need a re-do.
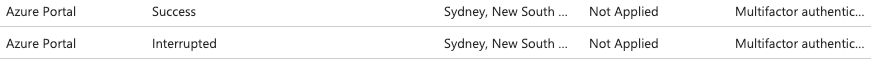
Second Test (License Applied - Redo)
So again I complete the following:
- Revoke Session tokens
- Proceed to https://www.office.com/
- Sign-out and forget the user.
- Sign-in again
Andddddddd, no MFA was prompted for, uh-oh, guess we need to dig a bit further. At this stage, I have signed in to other areas of M365 like the Azure Portal on this device that prompted for MFA, but the device I am on is NOT registered, and I had just reset all of my sessions so it should have prompted for a fresh MFA. I could even proceed to the now linked applications such as Outlook without any kind of MFA prompt. This time, I also revoked any multi-factor authentication sessions and going to try again on a other device. So the next test is:
- Revoke multi-factor authentication sessions
- Revoke Session Tokens
- Use a Different Device Type (Windows)
- Use a different browser (mozilla)
- Sign-in to https://www.office.com/
You guessed it, no MFA prompt again, just went straight to the "Stay Signed in" prompt.
Third Test (Per-user MFA)
So it appears at this stage that even though the user had registered themselves with MFA it will not work as of yet for OfficeHome direct sign-ins. Lets try to fix this issue by applying Per-user MFA.
- You can enable each account for per-user Microsoft Entra multifactor authentication. When users are enabled individually, they perform multifactor authentication each time they sign in (with some exceptions, such as when they sign in from trusted IP addresses or when the remember MFA on trusted devices feature is turned on).
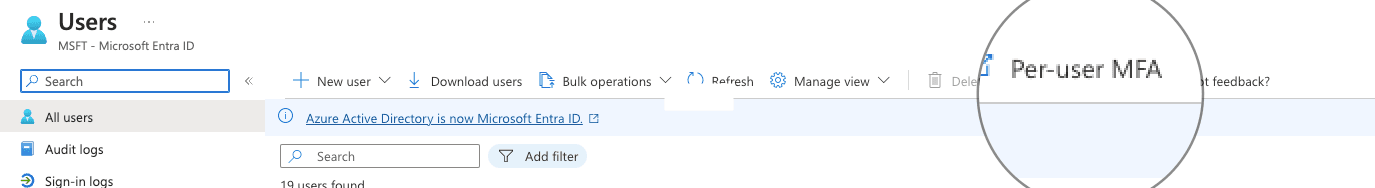
We observed that all users currently have a "MULTI-FACTOR AUTH STATUS" as "disabled". So lets fix our test user.
- Click user checkbox
- Click "enable"
This time when signing-in from the new device I was prompted for MFA!
I would recommend to set this to "Enforce" so that the MFA requirement is completely enforced. Note that Entra ID P1/P2 is required to enforce MFA to specific users otherwise you have to use "security defaults" which as observed did not work for OfficeHome authentications.
Fourth Test (Conditional Access)
Now for small business that might not have a Entra ID P1/P2 license they will likely need to enforce MFA in M365 as well as in the security defaults, as it appears that security defaults only enforces MFA for Azure. Since security defaults didnt work, Microsoft recommends using "Conditional Access" which is available for the following licenses:
- Microsoft 365 Business Premium
- Microsoft 365 E3 and E5
- Microsoft Entra ID P1 and Microsoft Entra ID P2 licenses
Here are the steps to set this up below:
- Disable your security defaults policy.
- Proceed to Identity -> Protection -> Conditional Access
- Create a new Policy (Note you can also create a group to do this instead of All Users)
- Users : All (you can choose to exclude your admin user for testing purposes and so you dont get locked out, but please make sure you have MFA in the future)
- Target resources: All cloud apps
- Access controls -> Grant -> Require multifactor authentication
- Enable Policy -> On
To test this one out now I also did the following actions to my user:
- Disabled the per-user MFA requirement
- Revoked Sessions
- Revoked MFA sessions
This appeared to have worked and prompted my user for MFA, this appears to be a good option for business without a P1/P2 License.
Fifth Test (Legacy Per-User M365 MFA)
The final option is to user the legacy per-user M365 MFA, although this is not recommended by Microsoft. This is available for any subscription although organisations should consider getting a better license for security purposes.
Test Controls:
- Deleted conditional access policy
- Revoked Sessions
- Revoked MFA Sessions
- Proceed to the Microsoft 365 Admin Center
- Go to Users -> Active Users
- Click on Multi-factor authentication

- Select the "Legacy per-user MFA" under the "not what you're looking for?" prompt.

- Select user(s) and click "enable"
Conclusion
At this stage even though the users had added a MFA device to their account during the initial set-up it does not mean that MFA is enabled for your Microsoft Cloud Apps too. One of the options below will also need to be applied by your administrators:
For organisations with P1/P2 licenses the administrators still need to ensure that "Identity -> All Users -> Per-user MFA" has a "MULTI-FACTOR AUTH STATUS" as "enabled" (preferably "enforced") for authentications to OfficeHome/M365 to prompt for MFA.
For smaller businesses that at least have Microsoft 365 Business Premium they will need to set-up a conditional access policy to ensure MFA is required for users authenticating to cloud apps.
Lastly, the legacy per-user MFA can be directly applied to users in Microsoft365 if all other options are unavailable, however a conditional access policy is recommended
I am not 100% sure if threat actors such as Tycoon/RaccoonO365 purposely target OfficeHome for their initial sign-ins because they are aware of the MFA complications or if it is a co-incidence. However, it is important to read up on MFA requirements and guides related to your license to prevent future unauthorised access. In a future blog I will test conditional access policies in an attempt to strengthen policies.
References:
- https://ig3thack3d4u.com/blog/RaccoonO365PAAS
- https://learn.microsoft.com/en-us/entra/fundamentals/security-defaults
- https://learn.microsoft.com/en-us/entra/identity/authentication/howto-mfa-userstates
- https://learn.microsoft.com/en-us/microsoft-365/admin/security-and-compliance/multi-factor-authentication-microsoft-365?view=o365-worldwide
- https://www.office.com/